shockingly simple crystals-dilithium zk proofs
⚓ General 📅 2025-01-17 👤 chance 👁️ 359Considerations when implementing zk proofs of crystals-dilithium signatures.
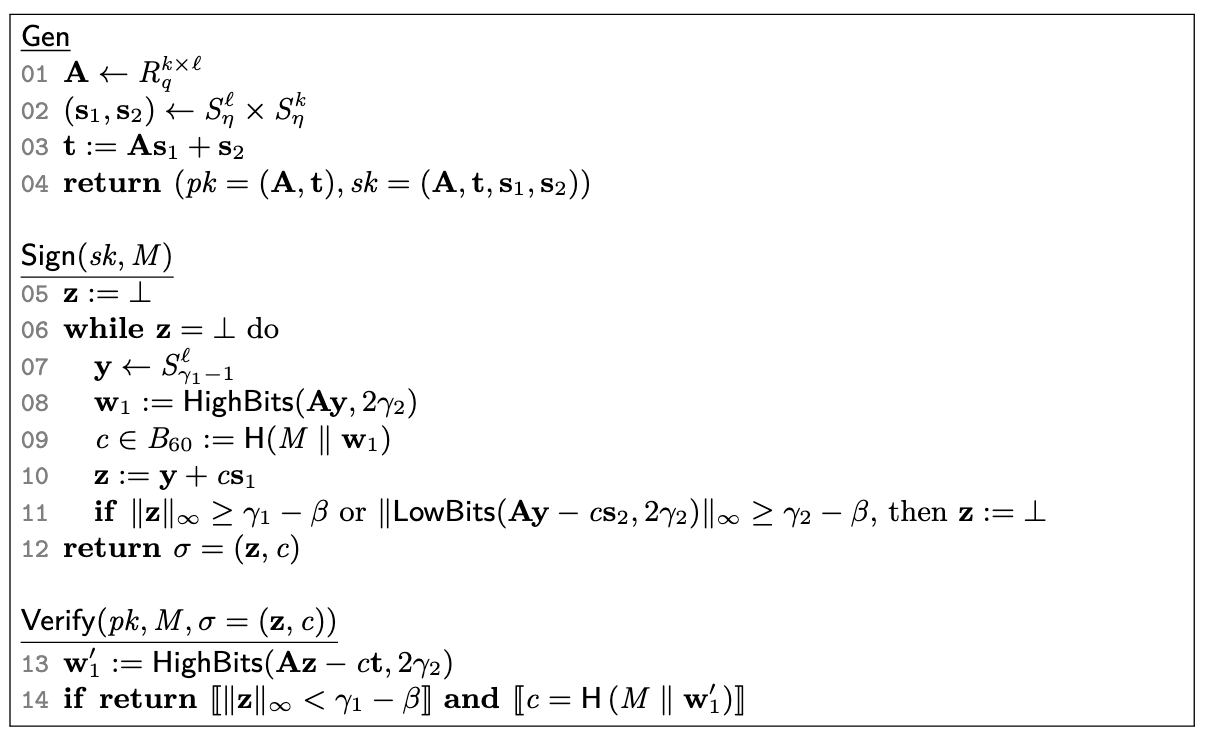
We’ll consider only the simplified scheme as described above. Discussion should be applicable to the full scheme.
Proving signature
With crystals-dilithium we must contend with a variable length signing procedure. Specifically we have to rejection sample based on the value of , and generate a ball polynomial based on a hash. Both of these operations are non-deterministic. e.g. it’s expected that they must be retried (specifically the authors target 4-7 iterations).
Inside a zk circuit we can avoid variable length execution by doing the rejection sampling at witness generation time and providing a suitable as an input. The circuit does not need to range check the value inside the proof. Outputting a value outside the range leaks the secret key, so it’s important that the witness calculation function operates correctly. In fact, we don’t need to constrain the calculation of the value either.
The verification procedure is robust and allows us to constrain relatively little of the signing procedure. Specifically we can take , , and as inputs directly.
We must constrain only the following:
- ( polynomial additions and polynomial multiplications) ()
unconstrained and calculation
The verifier calculates . We can substitute and in this equation to get
The middle terms cancel leaving
and are both of small norm and are filtered out by decomposing into the high bits of the coefficients yielding . Because the verifier calculates the value, it’s able to ensure that was hashed appropriately even without explicit constraints in the zk circuit.
misc notes
Polynomials are in a ring with modulus with coefficients in a field with scalar modulus .
Depending on the architecture of the execution system we can do lazy reduction for the scalar operations. This is a compiler level optimization that is particularly relevant in systems with large native types (e.g. ) that can’t efficiently support montgomery/crt representation.
🏷️ lattice, zk, signaturehackmd link with proper bold characters in formulas
Have to take a deeper look to this.
Please @![]() chance forward this to the PQ team!! You should also check in with Antonio Sanso from EF.
chance forward this to the PQ team!! You should also check in with Antonio Sanso from EF.
On a sidenote, the high-bits/low-bits split happens, you need to be sure that the distribution is randomly sampled. Otherwise, you’re at the risk of a significant security drop. At least this happens with regular ZKP world schemes.

